This section is a work in progress. Please reach out on our Discord if you have specific questions.
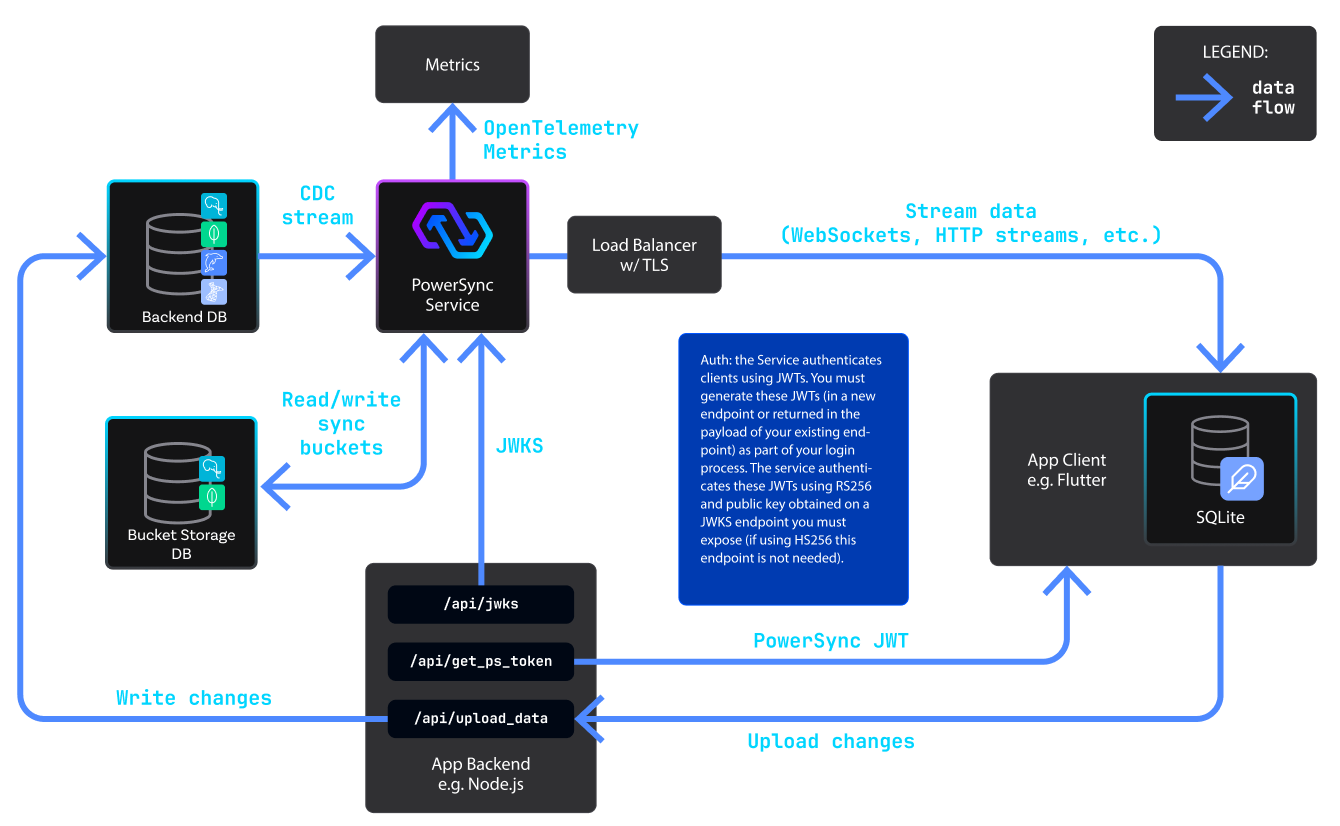
PowerSync Deployment Architecture
| Request Originator | Request Destination | Protocol |
|---|---|---|
| PowerSync Service | Postgres | TCP |
| PowerSync Service | MongoDB | TCP |
| PowerSync Service | OpenTelemetry Collector | TCP or UDP |
| PowerSync Service | JWKS Endpoint | TCP (HTTPS) |
| App Client | PowerSync Service (via LB) | TCP (HTTPS) |
| App Client | App Backend | TCP (HTTPS) |
| App Backend | Postgres | TCP |