- Allowing client-side write operations to be uploaded and applied to the backend database (Postgres, MongoDB, MySQL, or SQL Server). When you write to the client-side SQLite database provided by PowerSync, those writes are also placed into an upload queue. The PowerSync Client SDK manages uploading of those writes to your backend using the
uploadData()function that you defined in the Client-Side Setup part of the implementation. ThatuploadData()function should call your backend application API to apply the writes to your backend database. The reason why we designed PowerSync this way is to give you full control over things like data validation and authorization of writes, while PowerSync itself requires minimal permissions. - Authentication integration: Your backend is responsible for securely generating the JWTs used by the PowerSync Client SDK to authenticate with the PowerSync Service.
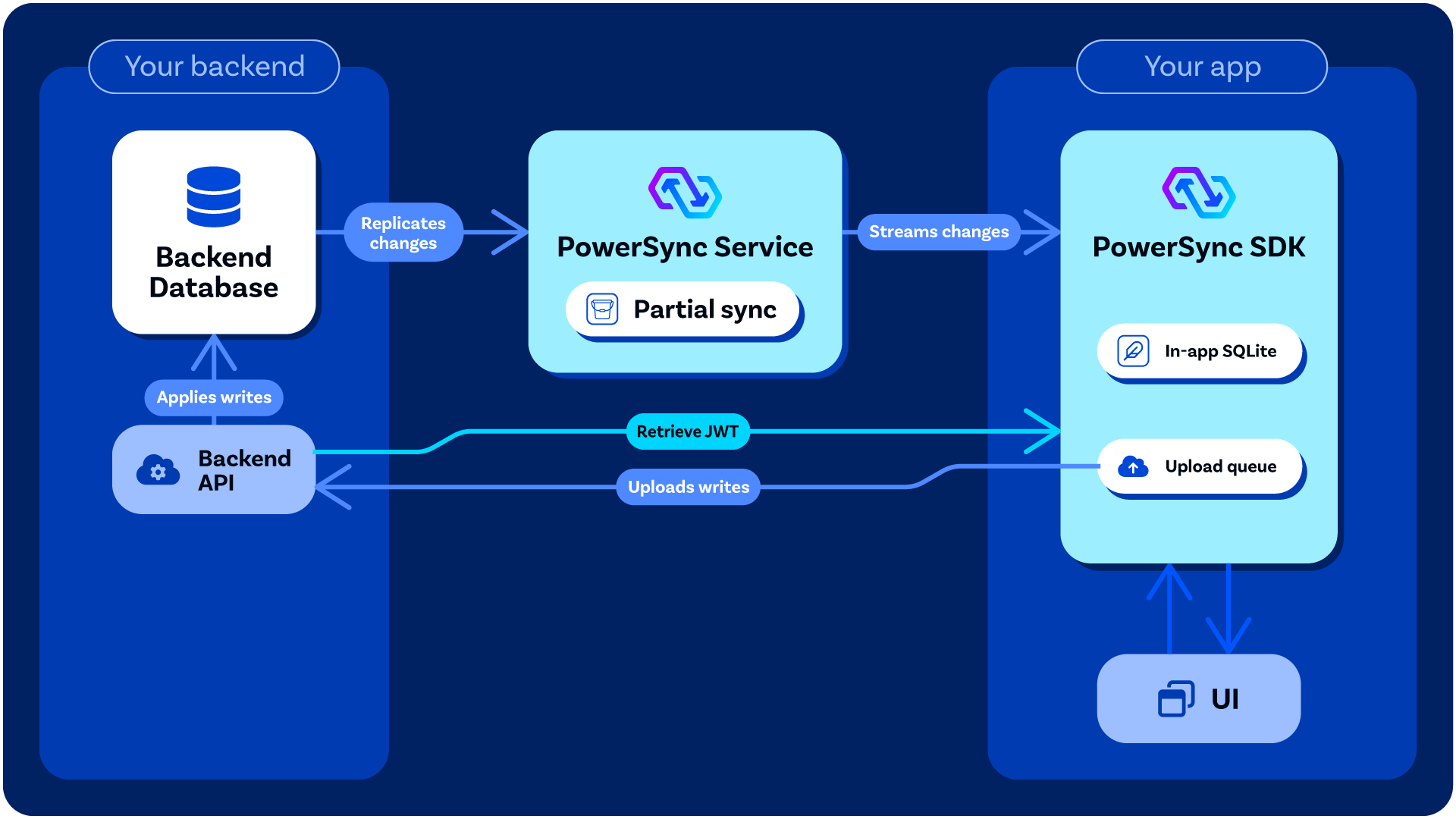
An overview of how PowerSync interacts with your backend application.
Processing Writes from Clients
The next section, Writing Client Changes, provides guidance on how can handle write operations in your backend application.Authentication
General authentication for your app users is outside the scope of PowerSync. A service such as Auth0 or Clerk may be used, or any other authentication system. PowerSync assumes that you have some kind of authentication system already in place that allows you to communicate securely between your client-side app and backend application. ThefetchCredentials() function that you defined in the Client-Side Setup can therefore call your backend application API to generate a JWT which can be used by PowerSync Client SDK to authenticate with the PowerSync Service.
See Authentication Setup for details.